On January 6th, 2025, the US Department of Health & Human Services (“HHS”) issued a combined Notice of Proposed Rulemaking (“Proposed Rule”) and Notice of Tribal Consultation relating to improvements to the HIPAA Security Rule to strengthen the cybersecurity of electronic protected health information (“e-PHI”). If finalized in its current form, the Proposed Rule will become final on or about March 7th, 2025. The Proposed Rule anticipates the adoption of significant modifications and enhancements to the force and effect of the current rules governing the implementation of HIPAA’s Security Rule.
Employer Action Items
- Review the NPRM: Employers should contemplate reviewing the text of the January 6th Proposed Rule, particularly those employers that qualify as HIPAA-covered entities (that is, plan sponsors of self-funded and level-funded medical, dental, vision, or carved-out pharmacy plans).
- Monitor Rulemaking Developments: Considering that the Proposed Rule is scheduled to become final on or about March 7th, HIPAA-covered entities should carefully and closely monitor HHS agency developments, keeping an eye out for the publication of the final rulemaking of the HIPAA Security Rule enhancements.
- Evaluate Present Security Posture: HIPAA-covered entities should utilize this intervening period to proactively review their security posture, evaluating the current performance of the currently prescribed security implementation specifications mandated to assure compliance with the Security Rule’s administrative, technical, and physical safeguards.
- Prepare for Change: Consistent with the requirements of the Proposed Rule and considering the recent frequency and the exploding exponential scope of cybersecurity incidents affecting the healthcare industry, plan sponsors and other covered entities should plan for the imminent release of final agency rulemaking from HHS, beginning their preparations for forthcoming modifications and expansions of compliance measures required in contemplation of the Proposed Rule’s range of new security standards and novel implementation specifications.
- Risk Analysis and Management: Finally, consistent with the current requirements of the Security Rule, covered entities should be prepared to demonstrate, in writing, their performance of a reasonable and appropriate risk analysis and risk management process in accordance with the current requirements of HIPAA’s Security Rule.
Summary
Rationale for the NPRM
According to a recent study, healthcare data breach costs to affected organizations have increased by more than 50 percent since 2020, making healthcare data breaches more expensive than data breaches in any other sector. The average cost of a healthcare data breach is almost $10.1 million.[1] Despite these costs, the consequences of out-of-date or non-existent security standards can be seismic. Such failures may lead to financial loss, reputational harm for affected individuals and regulated entities, privacy loss, and safety concerns.[2]
Additionally, breaches of unsecured PHI may lead to identity theft, fraud, stock manipulation, and competitive disadvantage.[3] According to a study funded by the Institute for Critical Infrastructure Technology, recovering from medical identity theft costs victims an average of $13,500.[4] Because, as explained in the NPRM, “…[u]nlike financial information, much of an individual’s PHI is immutable. For example, an individual’s date and location of birth and their health history will not change, even if their address might. In contrast, an individual’s passwords, bank account numbers, and other financial information can all be changed. Thus, PHI can continue to be exploited throughout an individual’s lifetime, making PHI likely to be far more valuable than an individual’s credit card information.”[5]
Overview of Provisions Contained within the NPRM
The NPRM proposes to strengthen the Security Rule’s standards and implementation specifications with new proposals and clarifications, including:[6]
- Remove the distinction between “required” and “addressable” implementation specifications and make all implementation specifications required with specific, limited exceptions.
- Require written documentation of all Security Rule policies, procedures, plans, and analyses.
- Update definitions and revise implementation specifications to reflect changes in technology and terminology.
- Add specific compliance time periods for many existing requirements.
- Require the development and revision of a technology asset inventory and a network map that illustrates the movement of ePHI throughout the regulated entity’s electronic information system(s) on an ongoing basis, but at least once every 12 months and in response to a change in the regulated entity’s environment or operations that may affect ePHI.
- Require greater specificity for conducting a risk analysis. New express requirements would include a written assessment that contains, among other things:
- A review of the technology asset inventory and network map.
- Identification of all reasonably anticipated threats to the confidentiality, integrity, and availability of e-PHI.
- Identification of potential vulnerabilities and predisposing conditions to the regulated entity’s relevant electronic information systems.
- An assessment of the risk level for each identified threat and vulnerability based on the likelihood that each identified threat will exploit the identified vulnerabilities.
- Require notification of certain regulated entities within 24 hours when a workforce member’s access to e-PHI or certain electronic information systems is changed or terminated.
- Strengthen requirements for planning for contingencies and responding to security incidents. Specifically, regulated entities would be required to, for example:
- Establish written procedures to restore the loss of certain relevant electronic information systems and data within 72 hours.
- Perform an analysis of the relative criticality of their relevant electronic information systems and technology assets to determine the priority for restoration.
- Establish written security incident response plans and procedures documenting how workforce members are to report suspected or known security incidents and how the regulated entity will respond to suspected or known security incidents.
- Implement written procedures for testing and revising written security incident response plans.
- Require regulated entities to conduct a compliance audit at least once every 12 months to ensure compliance with the Security Rule requirements.
- Require that business associates verify at least once every 12 months for covered entities (and that business associate contractors verify at least once every 12 months for business associates) that they have deployed technical safeguards required by the Security Rule to protect e-PHI through a written analysis of the business associate’s relevant electronic information systems by a subject matter expert and a written certification that the analysis has been performed and is accurate.
- Require encryption of e-PHI at rest and in transit, with limited exceptions.
- Require regulated entities to establish and deploy technical controls for configuring relevant electronic information systems, including workstations, in a consistent manner. New express requirements would include:
- Deploying anti-malware protection.
- Removing extraneous software from relevant electronic information systems.
- Disabling network ports in accordance with the regulated entity’s risk analysis.
- Require the use of multi-factor authentication, with limited exceptions.
- Require vulnerability scanning at least every six months and penetration testing at least once every 12 months.
- Require network segmentation.
- Require separate technical controls for backup and recovery of e-PHI and relevant electronic information systems.
- Require regulated entities to review and test the effectiveness of certain security measures at least once every 12 months in place of the current general requirement to maintain security measures.
- Require business associates to notify covered entities (and subcontractors to notify business associates) upon activation of their contingency plans without unreasonable delay, but no later than 24 hours after activation.
- Require group health plans to include in their plan documents requirements for their group health plan sponsors to comply with the administrative, physical, and technical safeguards of the Security Rule; ensure that any agent to whom they provide ePHI agrees to implement the administrative, physical, and technical safeguards of the Security Rule; and notify their group health plans upon activation of their contingency plans without unreasonable delay, but no later than 24 hours after activation.
Removal of “Addressable” Implementation Specification Designations
Perhaps most significantly, the Proposed Rule modifies the Security Rule’s current structural requirements underlying a covered entity’s adoption, implementation, and maintenance of reasonable and appropriate technical, physical, and administrative safeguards designed to protect the confidentiality, availability, and integrity of e-PHI. As a reminder, the Security Rule mandates the use of certain implementation specifications, respecting each standard identified for the Rule’s safeguard requirements.
The following graphic illustrates this concept. Following, we consider technical safeguards, of which there are five standards, numbered: (1) access controls, (2) audit controls, (3) integrity, (4) person or entity authentication, and (5) transmission security. Then, diving deeper, we review the individual implementation specifications under the access controls standard, of which there are four specifications, lettered: (a) unique user identification, (b) emergency access, (c) automatic logoff, and (d) encryption and decryption. Lastly, respecting a covered entity’s performance of its individual implementation specifications under each of the technical safeguard’s standards, note that each implementation specification (lettered “a” through “d”) identified in the following graphic identifies whether the standard is “required” or “addressable”:
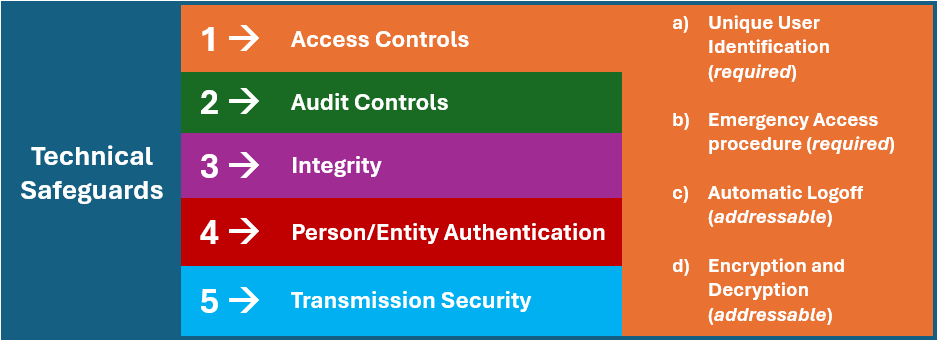
The question of whether a specific implementation specification (e.g., emergency access procedure, automatic logoff, etc.) is “required” or “addressable” is of significant consequence. Respecting each required implementation specification, the covered entity must perform and document a compliance assuredness process and policy respecting the adoption of the specific specification. However, respecting the “addressable” specifications, the covered entity must perform a risk analysis to evaluate whether and to what extent the individual specification must be adopted. So, while a covered entity must evaluate the adoption of an addressable standard, the entity is empowered to evaluate whether implementation of the individual specification is reasonable and appropriate given the size, scope, and complexity of the entity’s operations.
The discretionary evaluation process afforded to addressable implementation specifications provides covered entities with incredible flexibility in assessing, implementing, and administering an individualized security-related defensive posture. On the other hand, required implementation specifications leave little room for a covered entity to make such flexible elections, as these do not represent opportunities for discretionary adoption and implementation. It is precisely this flexibility and discretion that is questioned under the Proposed Rule because, as HHS notes in the Proposed Rulemaking, “…[w]e are concerned that regulated entities have focused their attention primarily on the cost of security measures, rather than considering the reasonableness and appropriateness of security measures in the context of all of the listed factors, including the probability and criticality of potential risks to e-PHI.”
Currently, of the forty-four (44) individual implementation specifications mandated under the current iteration of the Security Rule regulations, twenty-four (24) required specifications and twenty (20) addressable specifications. However, in comport with the Proposed Rule, all forty-four (44) of the current implementation specifications will become required in nature, thereby totally phasing out the “addressable” designations for twenty (20) individual implementation specifications. To further complicate compliance assuredness, the Proposed Rule also looks to add a bevy of new security standards while prescribing a range of novel implementation specifications to accompany the already existing forty-four (44) currently prescribed implementation specifications.
Conclusion
Plan sponsors and HIPAA-covered entities should carefully monitor developments respecting the Proposed Rule. If finalized as proposed, the final Security Rule will require significant financial and organizational resources for satisfactory implementation and administration. Small to mid-sized covered entities should be particularly cognizant of their responsibilities, as HHS has frequently referenced the tendency of these organizations to fail to perform the HIPAA’s Privacy and Security Rules requirements fully.
Additional Resources
[1] “Cost of a Data Breach Report 2023,” IBM, p. 13 (2023) (explaining that the average cost of a health care data breach was $7.13 million in 2020), https://www.ibm.com/reports/data-breach.
[2] “Report on Improving Cybersecurity In The Health Care Industry,” Health Care Industry Cybersecurity Task Force, p. 1 (June 2017), https://www.phe.gov/preparedness/planning/cybertf/documents/report2017.pdf.
[3] Id.
[4] See Hadi Ghayoomi, et al., “Assessing resilience of hospitals to cyberattack,” Digital Health, p. 3 (2021), https://doi.org/10.1177/20552076211059366.
[5] “HIPAA Security Rule To Strengthen the Cybersecurity of Electronic Protected Health Information,” US Department of Health & Human Services, Notice of Proposed Rulemaking, 45 CFR Parts 160 and 164 (2024).
[6] “HIPAA Security Rule Notice of Proposed Rulemaking to Strengthen Cybersecurity for Electronic Protected Health Information, Fact Sheet”, US Department of Health & Human Services (January 2025), HIPAA Security Rule Notice of Proposed Rulemaking to Strengthen Cybersecurity for Electronic Protected Health Information | HHS.gov.
For more information
We’re ready when you are. Get in touch and a friendly, knowledgeable Baldwin advisor is prepared to discuss your business or individual needs, ask a few questions to get the full picture, and make a plan to follow up.
This document is intended for general information purposes only and should not be construed as advice or opinions on any specific facts or circumstances. The content of this document is made available on an “as is” basis, without warranty of any kind. The Baldwin Insurance Group Holdings, LLC (“The Baldwin Group”), its affiliates, and subsidiaries do not guarantee that this information is, or can be relied on for, compliance with any law or regulation, assurance against preventable losses, or freedom from legal liability. This publication is not intended to be legal, underwriting, or any other type of professional advice. The Baldwin Group does not guarantee any particular outcome and makes no commitment to update any information herein or remove any items that are no longer accurate or complete. Furthermore, The Baldwin Group does not assume any liability to any person or organization for loss or damage caused by or resulting from any reliance placed on that content. Persons requiring advice should always consult an independent adviser.
The Baldwin Group offers insurance services through one or more of its insurance licensed entities. Each of the entities may be known by one or more of the logos displayed; all insurance commerce is only conducted through The Baldwin Group insurance licensed entities. This material is not an offer to sell insurance.






